10 Pro tips For Boosting Your Business’ Digital Security
Susie Morrow
#1: A Patch in Time Saves Crime
Malware, which is a portmanteau of the words, malicious and software, often works by riding on the back of software vulnerabilities. A vulnerability is sort of like a bug in the code, a hole that malware can hijack to help it install itself. Some malware even works silently. That is you can go to a website that has an ‘exploit kit’ within it. This kit looks for those vulnerabilities and installs malware, without you even being aware it’s happening.
Once the malware is installed you can end up with all sorts of bad things happening, from being held to ransom (ransomware) as all of your files have been encrypted, to having your bank login details stolen. To help prevent malware from taking over your system you need to make sure that any software you use, especially browsers, WordPress plugins, and operating system software, is up to date and fully patched. This removes most, if not all, of the known vulnerabilities and makes your computer a lot safer to use.
#2: Teach Yourself Phishing
Phishing is a massive problem today. Phishing involves receiving an email or SMS text from a well known company or a person you know. A phishing email will either contain an attachment, that it asks you to open, or encourage you to go to a website which looks just like the site of the company it is supposed to be from, where it will ask you to enter your login credentials. In the former case, if you open the attachment you’ll be infected with malware. In the latter case our login credentials will be stolen and used to logon to the real site.
Around 55% of all employees have been phished according to Symantec in their ‘Internet Security report 2016’. So it is a major problem and is responsible for around 95% of all security breaches according to the SANS Institute. One of the best ways to prevent phishing is to understand what a phishing email or text looks like, and to ensure anyone else in your company is also aware of the problem. Often phishing emails are hard to spot as the hackers who create them go to great lengths to make them look real.
I was spear phished recently. This is where the cybercriminal finds out about you, as a person, and uses this to make the scam more real. In my case, the phisher used a professional body I was a member of to contact me (using their messaging system). The message was specifically written to target me within that body, as it played on fears of reputational damage. It said that a Facebook page had been created by a person pretending to be me (the phisher gave a link to the page, which did exist and did say embarrassing things). They then offered to help me ‘sort it out’ as they had been also been a victim of identity theft. If I had not recognised the scam and had contacted this person, they would have asked for various identifying data, and used this to access things like my bank account and so on.
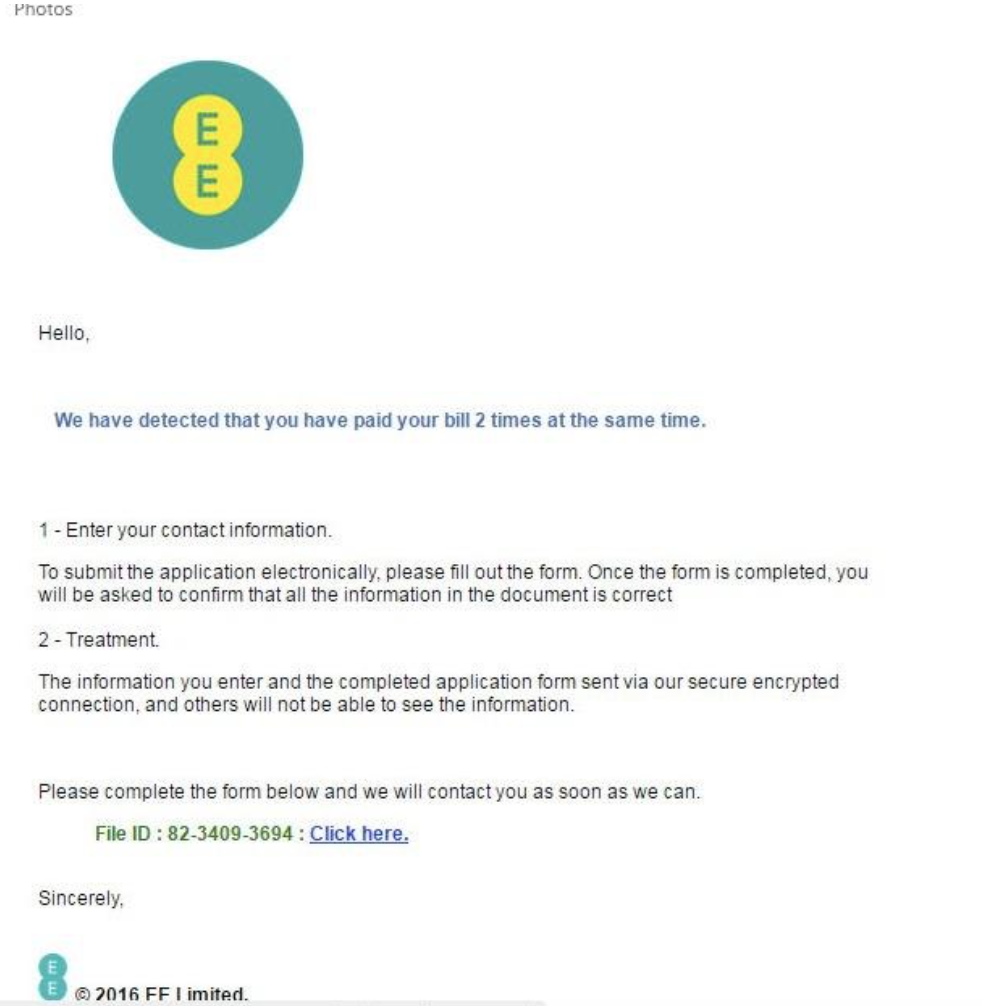
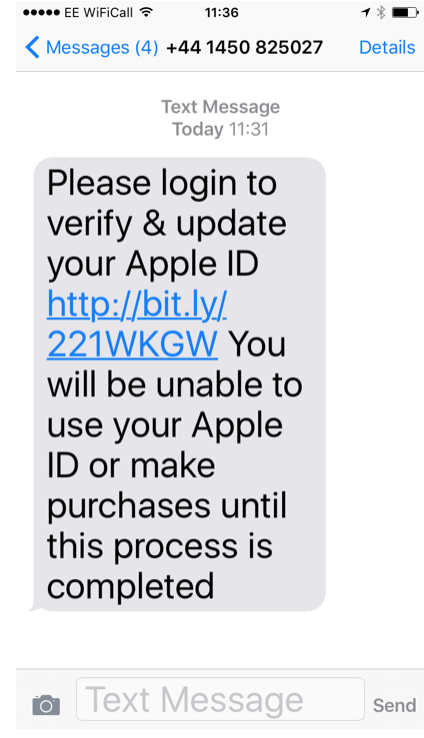
Below are some images of a typical phishing email and a typical SMiShing (SMS phishing) text message:
Note that the phishing email doesn’t have any personalisation, e.g. my name
SMiShing message (when checked the link went to a spoof site in Eastern Europe)
#3: Signed, Sealed and Delivered
More and more of us are creating digital contracts and using document signers to add our signature. There are lots of options out there that allow us to add a digital signature to a document or contract. However, not all of them are actually secure or have any real legal value. Digital signature technology has to be compliant with the laws that have been created to protect digitally signed documents; laws like UETA and ESIGN. Solutions like ApproveMe have been specifically built to add in a number of security features that make them compliant with these laws. This includes ensuring the digital signature is signed by the person it truly represents. Secure signing software also ensures that if anyone makes an unsolicited change to a document, it will be audited and a warning sent (this is possible using encryption techniques and hashing). If you want to digitally sign a document or contract, make sure you use a secure, legally binding solution.
#4: Two Factors are Better Than One
Another major security booboo that has given hackers a leg up in the world of cybercrime is the absence of second factor authentication or 2FA. You’ll know first factor authentication well – the dreaded password is an example of a first factor authentication. Second factor is when you add another, ‘second’ authentication method onto the first. For example, to login a person would enter a username and password AND would then have to enter an SMS code that’s sent to them.
Companies like Google and Twitter offer the use of 2FA to login in. The use of a second factor makes logging in MUCH more secure. It almost eradicates the effectiveness of a phishing scam that steals login credentials – the hacker can get your username and password from a spoof site, but they don’t have your mobile phone to pick up the code when it’s sent in an SMS. If you have the option (and you don’t always) setup a second factor to login to your accounts, especially sensitive ones, like bank accounts. If you have a person who looks after your server (for example your WordPress web server), make sure they use second factor to login to that server – many breaches happen through third party companies who are looking after servers and who only use a first factor and then get phished.
#5: Open Sesame: Passwords and How to Use Them
If you don’t have the option of using 2FA then you need to make sure the passwords you use are as secure as they can be. Passwords are never going to be truly secure when phishing exists, even the strongest password in the world won’t withstand a successful phishing attack. But you can do certain things to prevent other security issues like ‘brute force attacks’, where a person’s password is found by simply using a special computer program to work out what it is. Brute force attacks have a starting point of a commonly used password and password patterns. SplashData have analysed the most common passwords, so you can avoid them. Passwords like 123456, password, and qwerty are the most common, make yours special.
There is also the problem of hackers stealing usernames and passwords, en masse, from servers. People often will use the same username (which may be an email address) and password across many different services. Once a hacker has the password to one system, they have the keys to the kingdom of many of the others. The best way to avoid having lots of your accounts compromised is to vary your passwords across accounts.
A useful site to check out to see if you have had any accounts breached is here: https://haveibeenpwned.com/
#6: Anti-Virus – To Have or Have Not
Anti-virus software isn’t as effective as it used to be. Antivirus vendor Symantec have even admitted as much saying that only 45% of malware is prevented by AV software. However, it is still important to use AV software as 55% of malware is stopped by running an antivirus application. But make sure your AV software is up to date and is running the latest definitions.
#7: Love me Love My Privacy
Cybercriminals are targeting your data. They are after something known as Personally Identifying Information’ or PII because they can sell it on the dark web for lots of $$’s; certain data records, like healthcare records go for the most. The Ponemon Institute found that the average price paid for a stolen healthcare record was $363. Be careful about who you release your information too – there are an estimated 15 million U.S. citizens who have their identity stolen each year. Make sure that if you can set privacy settings, that you do so. Facebook for example is notorious for not applying the highest privacy settings by default. Even if you do set higher level privacy on Facebook, anything shared by a friend then comes under their privacy settings and so on; very quickly information can be disseminated.
It’s also a good idea to subscribe to an identity protection scheme with a company like Experian or another credit file agency. You will be notified if anyone tries to use your identity details to setup a loan, for example.
#8: The Ring of Fire
Many threats come in from web based sources. Web servers, such as the one that runs your website are a prime target for certain attack types. A modern web based firewall will prevent all of the well-known attacks. To find out more about web based attacks check out the Open Web Application Security Project or OWASP. They do a ‘top ten’ web threats most years which looks at what are the most used web attacks that cybercriminals are using. Web application firewalls or WAFs are built to protect against the OWASP top ten.
#9: Be Mobile Aware
Mobiles are becoming increasingly targeted by hackers. This isn’t surprising when you know that in 2014, the smartphone took over the desktop as the main device used to access the Internet. And according to PEW Research, 57% of Americans use their smartphone to do Internet banking. The smartphone is therefore bound to be a heavy target for cybercrime going forward. One of the best ways you can protect yourself from mobile based attacks is to be aware – don’t use public Wi-Fi spots to access anything at all sensitive, or that requires you to enter login credentials. I use a personal Wi-Fi device if I travel which requires a password – it’s like having your own home or office Wi-Fi in your pocket.
Also, be careful of apps you download. Malware can be hidden in an app. The worst affected phones are Android where it is estimated 97% of malware is targeted. But don’t get too complacent if you have an iPhone as Apple is starting to be more heavily targeted too. Avoid downloading apps from anywhere other than the official app stores.
#10: There’s Always a Man in The Middle
A very common technique used by hackers to steal information is known as a Man in the Middle (MitM) attack. It is possible to grab data during a web transaction if the website is not correctly secured. You can tell if a website is secure as it will have an HTTPS and NOT an HTTP at the front of the URL, e.g. https://www.approveme.com/e-signature and NOT https://www.approveme.com/e-signature. All pages of the site should have an HTTPS, especially those where you enter information and credentials.
MitM attacks don’t just steal information, they can change it too. So, for example, if you were carrying out a transaction that involved $100, it could be changed to $10,000. It might sound like it’s hard to do, but it really isn’t. In fact you can even buy a $100 device, used legitimately by security testers, called the Wifi Pineapple, which allows you to carry out a MitM from the comfort of your own local cafe.